Updated:
Introduction
In an increasingly digitized world, the importance of cybersecurity can’t be overstated. Our virtual spaces, once the exciting frontier of technology, have now become battlegrounds for information warfare, with email often being the primary channel of communication exploited in cyber attacks.
According to the FBI’s Internet Crime Complaint Center, phishing was the most common type of cybercrime in 2020, and there has been a steady rise in phishing attacks year over year. Notably, cybercriminals have proven time and again that no domain, regardless of its prestige or security measures, is immune to their tactics.
Phishing thrives on trust, and the sense of security a familiar domain name can provide. An email received from a .gov, .edu, or reputable .com domain might seem unquestionably trustworthy to an unsuspecting user. This trust, however, can be brutally exploited by threat actors, if domains are not adequately secured.
In this article, we focus on email security, specifically Sender Policy Framework (SPF) and Domain-based Message Authentication, Reporting & Conformance (DMARC), two of the most critical email security measures. By examining over 1 million domains, we aim to highlight common security misconfigurations that could leave these domains, and thereby their users, vulnerable to phishing attacks.
Our hope is to shed light on the current state of email security, the implications of misconfigured SPF and DMARC records, and the urgent need for improved domain security across the board. Join us as we delve into our key findings and insights gleaned from our expansive data set, and explore what they mean for the future of email security.
Stay tuned as we unpack the depth of this problem and arm you with the knowledge you need to better protect your domains and your users.
The Problem
Phishing attacks have been a persistent thorn in the side of cybersecurity, with attackers regularly exploiting the trust placed in familiar domain names to deceive recipients. As the gatekeeper for inbound emails, email security measures such as the Sender Policy Framework (SPF) and Domain-based Message Authentication, Reporting & Conformance (DMARC) play a crucial role in protecting domains and their users from phishing attacks.
SPF and DMARC are email authentication methods designed to prevent spammers from sending emails on behalf of your domain. With properly configured SPF and DMARC records, you can specify which mail servers are allowed to send email on behalf of your domain and define a policy for how receiving mail servers should handle mail that fails authentication.
However, misconfigured SPF and DMARC records can inadvertently leave the door open for phishing attacks. For instance, an SPF record that ends in “+all” or “?all” is, in effect, an open invitation for anyone to use the domain to send email. Without a correctly configured DMARC record, these messages could arrive in the recipient’s inbox without any indication that they were not sent from a legitimate source.
It is worth In some cases, the email client might add a small note indicating that the email was sent ‘via’ another domain. However, this subtle warning is easy to overlook or make look legitimate, especially for unsuspecting users who might not be familiar with what such a message signifies.
For this study, we focused specifically on SPF and DMARC misconfigurations that can lead to phishing attacks. While other technologies like DomainKeys Identified Mail (DKIM) play a role in email security, they are more aligned with protecting against man-in-the-middle (MITM) attacks and hence are outside the scope of this research.
Our aim here is to emphasize that SPF and DMARC misconfigurations can render these protective measures ineffective, leaving domains and their users vulnerable to phishing attacks. Let’s delve into the methodology we employed to shed light on the extent and implications of this issue.
Methodology
In this study, we focused on over 1 million domains, sourced from Cloudflare Radar. Cloudflare is renowned for its strong anti-spam detection capabilities, which contributed to the reliability of our dataset, though it is important to acknowledge that no system is entirely immune to false positives or negatives.
To ensure we were analyzing real, active websites, and not spam-populated domains, we used Google’s DNS servers to resolve the domains. Out of the initial million, only 310,639 domains responded with valid records.
A significant aspect of our methodology was the use of a scalable, internally developed microservice rather than a more conventional, rapid tool like massdns. This choice was driven by a commitment to accuracy over speed. Each instance of our infrastructure resolved 100 domains synchronously, with a generous timeout of 5 seconds per domain and an additional retry to ensure resilience.
At the height of data gathering, our infrastructure scaled up to 300 instances operating simultaneously. This approach ensured that we cast a wide net and captured a comprehensive view of the current state of domain security without missing records or being rate-limited by the DNS servers.
During our analysis, we found many domains with high-risk Top-Level Domains (TLDs). These domains, numbering 25,377, were likely the result of some manipulation of the top domains list. However, their inclusion or exclusion didn’t significantly affect the overall statistics, shifting results by less than 1% in any tests conducted.
Having collected the data, our next step was to analyze and categorize it based on various parameters defining “phishability”. In the upcoming section, we share our key findings and the implications of these SPF and DMARC misconfigurations.
Key Findings
The results of our study revealed significant vulnerabilities in email security across a variety of domain types and regions. Here are the key findings:
1. Vulnerabilities Across Domain Types
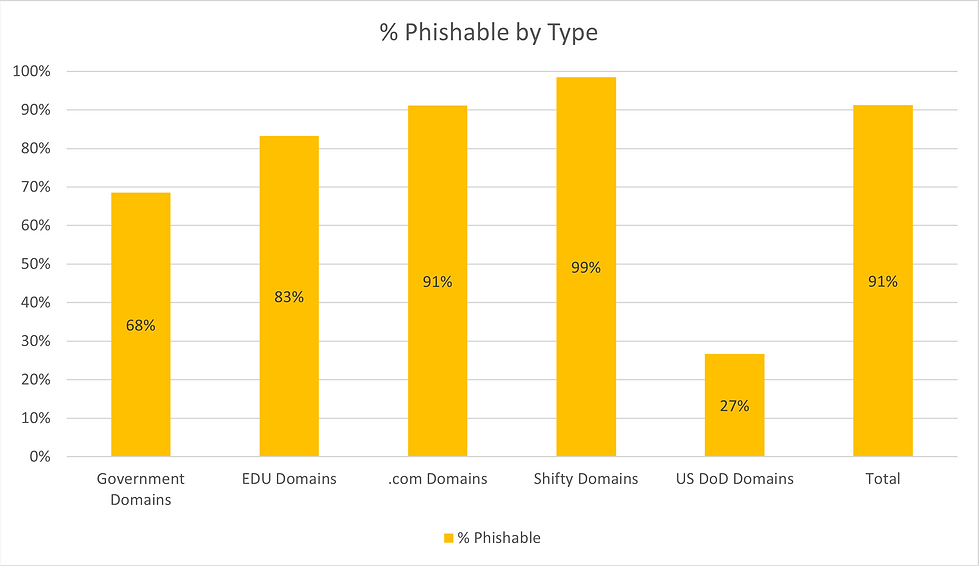
Out of the domains analyzed, we found that a large percentage were phishable due to SPF and DMARC misconfigurations. Our definition of phishable includes domains with SPF ending with “+all” or “?all”, and domains with no or invalid DMARC.
For instance, 68.49% of government domains, 83.24% of .edu domains, 91.11% of .com domains, and a staggering 98.53% of high-risk TLDs fell into the phishable category. Even within the domains managed by the US Department of Defense, 26.67% were deemed phishable.
Most concerning were the 649 domains that had a “+all” tag in their SPF. These domains are not just phishable but REALLY phishable, as they essentially allow anyone to send emails on their behalf with absolutely 0 indicators. It would even be better to have no SPF or DMARC records at all.
2. Vulnerabilities by Country
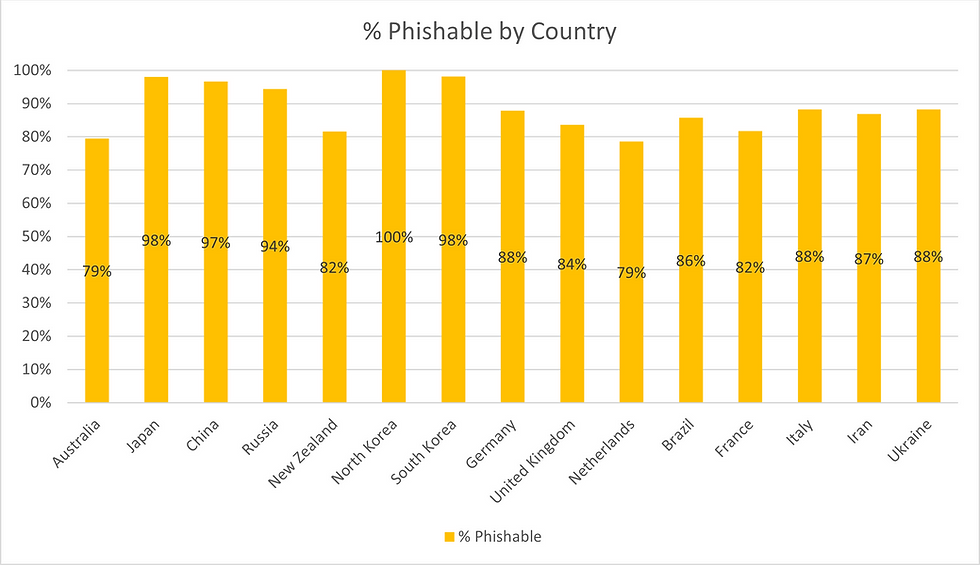
When examining domains on a country-by-country basis, we found similar vulnerabilities. Countries like Japan (97.99%), South Korea (98.11%), and China (96.59%) had a high percentage of phishable domains. Even in countries with relatively lower percentages, such as Australia (79.47%) and the Netherlands (78.59%), the potential for phishing was still significant.
A few countries stood out due to the number of domains that had the extremely insecure “+all” tag in their SPF. For instance, France had 24 such domains, with an inexplicable lead on the second highest, Italy with 5.
3. Misconfigurations and Invalidation
Misconfigurations in SPF and DMARC records were found to be alarmingly common, often leading to invalidation. For instance, 864 domains were invalidated due to SPF records not starting with “v=spf1”. The most common reasons for this were accidental misplacements, such as starting the record with quotes or missing spaces.
In the case of DMARC, 115 records were ignored because they didn’t start with “v=DMARC1”, most often due to quotes at the start or random characters from copy-paste issues.
These findings underscore the scale and depth of the problem that misconfigurations of SPF and DMARC records pose for domain security and the protection of users from phishing attacks. In the next section, we will delve into specific case studies to further illustrate these issues.
Case Studies: A Closer Look at Notable Domains
To illustrate the real-world implications of our findings, let’s examine a few notable examples that span different domain types and countries:
1. The Lone North Korean Domain
North Korea is represented by a single domain in our dataset: the Ministry of Foreign Affairs (mfa.gov.kp). Despite being the sole representative, this domain falls into the phishable category due to its lack of email security configurations, they do not employ SPF or DMARC records at all.
To really illustrate this point, I sent a test email from our phishing infrastructure to myself as this domain (written by ChatGPT, as lots of phishing is now):
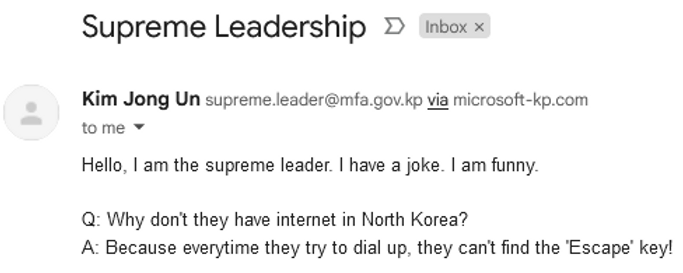
* Note the “via” tag, it’s not obvious that it’s phishing, and very easy to pick a domain that fits in there.
2. Government and Education Institutions
Alarmingly, 68% (1,113) of government websites and 83% (993) of education (.edu) sites can potentially be phished. Even ministries of education, like those in Italy and Saudi Arabia, were not exempt from misconfigurations. The Italian Ministry of Education, for instance, has SPF but no DMARC, leaving it vulnerable to phishing.
3. Energy and Science Institutions
Energy and science institutions also present examples of email security vulnerabilities. Iran’s Ministry of Energy domain has a soft fail SPF and no DMARC, while the Frankfurt University of Science (frankfurt-university.de) has neither SPF nor DMARC in place.
4. The Case of ‘+all’ Policies
While fewer domains have ‘+all’ policies, those that do allow transparent phishing. Such domains are not just phishable, they’re REALLY phishable due to absolutely 0 indicators of phishing. This configuration was even found in government domains, such as Greece’s employment services domain (DYPA). There were a total of 649 domains with ‘+all’, demonstrating a serious lack of awareness of this configuration’s risks.
The +all issues are as bad as it gets since there’s no indication at all compared to the above. To illustrate the point, compare this email sent from “DYPA” to me:
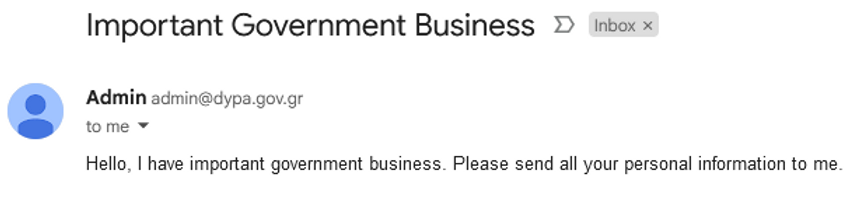
These case studies exemplify the broader trends our study uncovered. Misconfigurations in SPF and DMARC records, particularly those that make a domain phishable, are surprisingly common across a wide range of institutions and countries. In the final section, we discuss the implications of these findings and suggest potential strategies to address these security vulnerabilities.
Mitigation Strategies
The findings from our analysis clearly illustrate the pervasive issue of email security misconfigurations across a multitude of domains. These vulnerabilities can be easily exploited by malicious actors for phishing attacks, potentially leading to serious consequences such as data breaches, financial loss, and reputational damage.
Fortunately, there are steps that organizations can take to mitigate these risks and strengthen their domain security:
1. Review and Correct SPF and DMARC Records
The first and most important step is to ensure that your SPF and DMARC records are correctly configured. Pay particular attention to avoid configurations that can make your domain phishable, such as “+all” or “?all” in your SPF, or invalid DMARC settings.
If your domain’s SPF does not end with “-all”, consider revising it. This tag tells email receivers to fail messages that don’t originate from your specified hosts, preventing others from using your domain in phishing attacks.
In addition, make sure your DMARC is correctly set up. A missing or invalid DMARC leaves your domain vulnerable to phishing. The DMARC record should start with “v=DMARC1” and include the necessary tags, especially the “p=” tag that tells receivers what to do with messages failing DMARC checks.
2. Regular Audits and Testing
It’s crucial to regularly audit your email security configurations for any misconfigurations or vulnerabilities. Regularly test your email security using a reputable testing tool to ensure your SPF, DKIM, and DMARC are working as expected.
3. Training and Awareness
Educate your team about the importance of email security and the risks associated with misconfigured SPF and DMARC records. The more aware your team is of these issues, the more vigilant they’ll be in preventing such misconfigurations.
4. Seek Expert Assistance
If you’re unsure about how to configure SPF and DMARC records or improve your email security, consider seeking the assistance of experts or a cybersecurity firm. This can be especially helpful for organizations that lack the necessary technical expertise in-house.
Conclusion
Our comprehensive analysis of over a million domains highlights the ubiquity of email security misconfigurations, particularly in SPF and DMARC records. It underscores the widespread susceptibility to phishing attacks, an alarming reality in our increasingly digital world. Whether they represent government institutions, educational bodies, or commercial entities, domains across various categories and countries remain vulnerable to these cyber threats.
However, it’s important to emphasize that this problem is not insurmountable. The vulnerabilities we’ve identified are largely due to misconfigurations or oversights that can be addressed with the right knowledge and effort. By taking proactive measures such as correcting SPF and DMARC configurations, conducting regular audits, fostering cybersecurity awareness, and seeking expert assistance when needed, organizations can significantly bolster their email security.
In an era where digital communication has become indispensable, maintaining robust email security is not just a luxury—it’s a necessity. As we move forward, let’s ensure we stay vigilant and proactive in protecting our domains, preserving the integrity of our digital communication, and securing a safer future in cyberspace.
At Stratus Security, we’re committed to supporting organizations in this endeavor. We believe in building a safer digital landscape—one domain at a time.
To continue this conversation or to learn more about how we can help secure your domain, please feel free to reach out to us. We look forward to joining forces in strengthening your security.