Blog
-
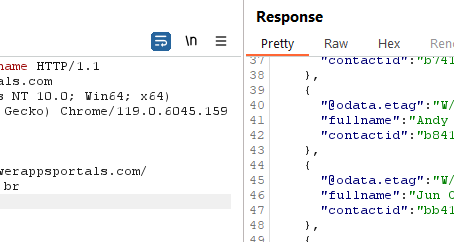 December 31, 2024
December 31, 2024Discovery to Resolution: A Critical Microsoft 365 Vulnerability
Updated: Jan 3Our latest exploration has uncovered critical vulnerabilities within Microsoft 365, highlighting significant security risks that could compromise sensitive business data. These vulnerabilities expose.
-
 February 22, 2024
February 22, 2024Hiring Penetration Testing Services: 7 Things To Consider
Updated: Penetration testing has become a crucial part of any organization's cybersecurity strategy. With data breaches costing companies millions of dollars in losses each year,.
-
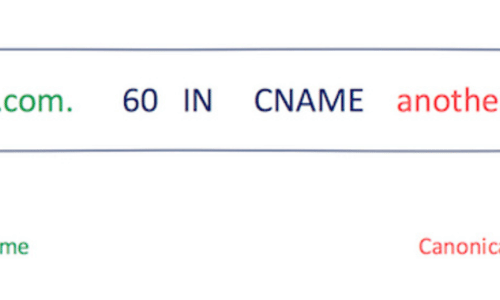 January 11, 2024
January 11, 2024A Comprehensive Guide to Subdomain Takeovers
Updated: Subdomain takeovers are becoming a part of daily life for businesses but the understanding of the risks and detection methods are widely misunderstood. When.
-
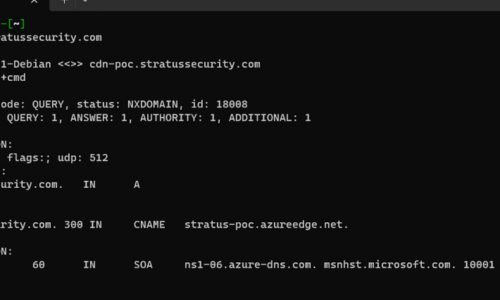 January 11, 2024
January 11, 2024Microsoft Azure Subdomain Takeover Guide
Updated: As a penetration tester or bug bounty hunter, subdomain takeovers are one of the most common vulnerabilities to show up but they are also.
-
 January 11, 2024
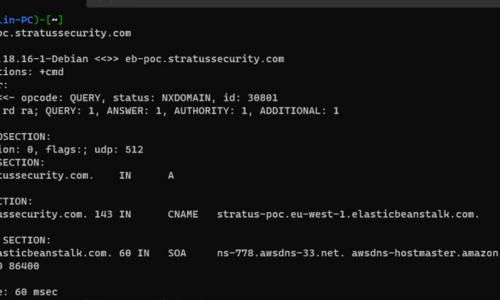
January 11, 2024Amazon Web Services (AWS) Subdomain Takeover Guide
Updated: In this post, we will explore AWS services that can be taken over. For a deeper look at subdomain takeovers as a whole, check.
-
 December 14, 2023
December 14, 2023Understanding GRC in Cyber Security
Updated: Governance, risk management, and compliance (GRC) have become crucial elements of cyber security strategies for organizations of all sizes. With the digital landscape evolving.
-
 December 11, 2023
December 11, 2023The Ultimate Subdomain Takeover Tool
Updated: Today we are telling the story of how we developed a cyber security tool to find subdomain takeovers and why the existing solutions just.
-
 October 10, 2023
October 10, 2023AICD Cyber Security Governance Principles: A Guide for Directors
Updated: Introduction Cyber threats have never been more prevalent or sophisticated than they are today. In 2023, cybercrime is predicted to cost the global economy.
-
 June 12, 2023
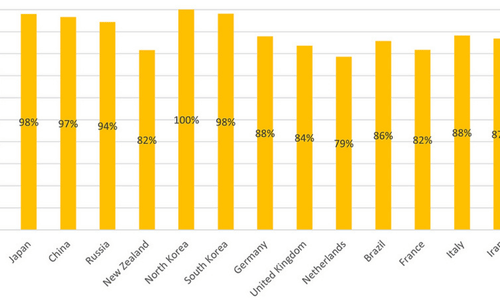
June 12, 2023Email Security: An In-Depth Analysis of the Top 1 Million Domains
Updated: Introduction In an increasingly digitized world, the importance of cybersecurity can't be overstated. Our virtual spaces, once the exciting frontier of technology, have now.
-
 April 27, 2023
April 27, 2023Understanding Penetration Testing: External Network Security 101
Updated: Introduction Importance of External Network Security Almost all businesses rely heavily on their external networks to communicate, collaborate, and operate efficiently. With the ever-increasing.
-
 April 17, 2023
April 17, 2023Understanding Penetration Testing: Web Application Security 101
Updated: Introduction These days, ensuring the security of your web applications is more critical than ever. With cyber threats constantly evolving, businesses must be proactive.
-
 April 11, 2023
April 11, 2023The Ultimate Guide to Penetration Testing: What Businesses Need to Know.
Updated: In today's rapidly evolving digital landscape, cybersecurity has become a top priority for businesses of all sizes and industries. As cyber threats.
-
 December 31, 2024
December 31, 2024Discovery to Resolution: A Critical Microsoft 365 Vulnerability
Updated: Jan 3Our latest exploration has uncovered critical vulnerabilities within Microsoft 365, highlighting significant security risks that could compromise sensitive business data. These vulnerabilities expose.
-
 February 22, 2024
February 22, 2024Hiring Penetration Testing Services: 7 Things To Consider
Updated: Penetration testing has become a crucial part of any organization's cybersecurity strategy. With data breaches costing companies millions of dollars in losses each year,.
-
 January 11, 2024
January 11, 2024A Comprehensive Guide to Subdomain Takeovers
Updated: Subdomain takeovers are becoming a part of daily life for businesses but the understanding of the risks and detection methods are widely misunderstood. When.
-
 January 11, 2024
January 11, 2024Microsoft Azure Subdomain Takeover Guide
Updated: As a penetration tester or bug bounty hunter, subdomain takeovers are one of the most common vulnerabilities to show up but they are also.
-
 January 11, 2024
January 11, 2024Amazon Web Services (AWS) Subdomain Takeover Guide
Updated: In this post, we will explore AWS services that can be taken over. For a deeper look at subdomain takeovers as a whole, check.
-
 December 14, 2023
December 14, 2023Understanding GRC in Cyber Security
Updated: Governance, risk management, and compliance (GRC) have become crucial elements of cyber security strategies for organizations of all sizes. With the digital landscape evolving.
-
 December 11, 2023
December 11, 2023The Ultimate Subdomain Takeover Tool
Updated: Today we are telling the story of how we developed a cyber security tool to find subdomain takeovers and why the existing solutions just.
-
 October 10, 2023
October 10, 2023AICD Cyber Security Governance Principles: A Guide for Directors
Updated: Introduction Cyber threats have never been more prevalent or sophisticated than they are today. In 2023, cybercrime is predicted to cost the global economy.
-
 June 12, 2023
June 12, 2023Email Security: An In-Depth Analysis of the Top 1 Million Domains
Updated: Introduction In an increasingly digitized world, the importance of cybersecurity can't be overstated. Our virtual spaces, once the exciting frontier of technology, have now.
-
 April 27, 2023
April 27, 2023Understanding Penetration Testing: External Network Security 101
Updated: Introduction Importance of External Network Security Almost all businesses rely heavily on their external networks to communicate, collaborate, and operate efficiently. With the ever-increasing.
-
 April 17, 2023
April 17, 2023Understanding Penetration Testing: Web Application Security 101
Updated: Introduction These days, ensuring the security of your web applications is more critical than ever. With cyber threats constantly evolving, businesses must be proactive.
-
 April 11, 2023
April 11, 2023The Ultimate Guide to Penetration Testing: What Businesses Need to Know.
Updated: In today's rapidly evolving digital landscape, cybersecurity has become a top priority for businesses of all sizes and industries. As cyber threats.