Updated:
Subdomain takeovers are becoming a part of daily life for businesses but the understanding of the risks and detection methods are widely misunderstood. When looking through the HackerOne Hacktivity feed there are always plenty but they are largely ignored outside bug bounties.
These vulnerabilities can pose significant risks to both the security and reputation of an organization. This guide is designed to provide a comprehensive understanding of subdomain takeovers, including identification, risk, exploitation, prevention, and response strategies.
What is a Subdomain Takeover?
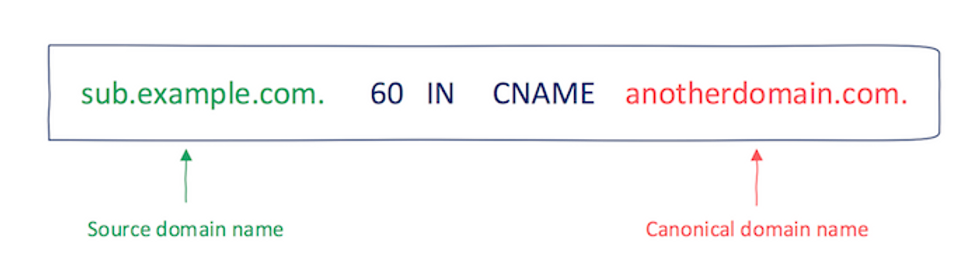
A subdomain takeover occurs when an attacker gains control of a subdomain of a legitimate website. This happens when a subdomain, which should point to a specific web service (like a hosting platform, cloud service, or CDN), ends up pointing to a service that’s been decommissioned or abandoned, while the DNS record still exists. Attackers exploit these lingering DNS entries to divert the subdomain traffic to their servers.
Imagine your company previously used blog.yourcompany.com for a hosted blog. If you stop using the service but don’t update the DNS record, an attacker could hijack this subdomain. Visitors to blog.yourcompany.com might then land on a page controlled by the attacker which could be used for malicious purposes.As a penetration tester or bug bounty hunter, subdomain takeovers are one of the most common vulnerabilities to show up but they are also one of the quickest to be snapped up in bug bounties due to modern automation.
How Do They Happen?
Subdomain takeovers typically happen when a subdomain is still pointing to a web service that has been removed, deleted, or otherwise made inactive. This misalignment leaves the subdomain vulnerable to being claimed by unauthorized parties.
Specifically, the common causes are:
-
- Expired Domains: For example, subdomain.example.com is pointing to example-old.com but example-old.com expires. A malicious actor can register example-old.com and host anything they want on there and subdomain.example.com will be pointing to this new, malicious content.
-
- Unused SaaS Provider Resources: For example, a company uses subdomain.example.com for a project hosted on GitHub Pages. After abandoning the project, the company deletes the GitHub Pages site but neglects to remove the corresponding DNS records. Despite the original site no longer existing, subdomain.example.com continues pointing to the now vacant GitHub Pages address, creating an opportunity for attackers to claim and redirect it.
At the heart of subdomain takeovers is the mishandling of subdomains that are left pointing to reclaimable resources or expired domains. Implementing thorough subdomain hygiene practices, such as regularly monitoring expiration dates, deleting unused applications or buckets, and auditing for inactive subdomains, is essential to prevent these vulnerabilities.
What Are The Risks?
Subdomain takeovers can pose significant security risks if exploited by attackers. Here are some of the main risks:
-
- Phishing attacks – If an attacker takes over a subdomain, they can create fake login pages and other phishing schemes to steal user credentials and sensitive information. Users are more likely to trust phishing pages hosted on a valid company subdomain.
-
- Serving malware – Attackers can host malware payloads on a taken over subdomain and distribute them to users. This allows them to bypass firewalls and other security filters that may block access to malicious domains but allow access to the compromised company subdomain.
-
- Defacement – A taken over subdomain could be used to deface the website by redirecting visitors to disturbing or offensive content. This could harm the company’s reputation.
-
- SEO impact – If search engine crawlers find inappropriate or spammy content on the compromised subdomain, it could negatively impact the company’s search engine rankings.
-
- Browser cookie theft – Attackers could create scripts to steal browser cookies for the parent domain from users who visit the compromised subdomain site. This gives them access to user accounts.
-
- Network pivoting – Access to an internal company subdomain provides a foothold into the corporate network that attackers can use to try and move laterally to access other systems and data.
Identifying Vulnerable Subdomains
There are several methods that can be used to identify subdomains that may be vulnerable to takeovers. You could use manual enumeration of DNS records using tools like dig, host and dnsrecon but these days there are plenty of great tools to do all the hard work for you.
For example, we have created a tool like no other to detect subdomain takeovers, you can find it here in our GitHub.
The methodology to find subdomain takeovers on a given domain is finding subdomains, analyzing their DNS records and exploitation as outlined below.
1. Subdomain enumeration – This involves using various tools and techniques to discover as many subdomains associated with a domain as possible. Some common subdomain enumeration techniques include brute forcing subdomains, searching certificate transparency logs, scraping search engine results, and using open-source intelligence (OSINT) tools. A personal favourite here at Stratus is the Subfinder tool from Project Discovery.
2. Analyze DNS records – Once a list of subdomains has been compiled, the next step is to analyze the DNS records associated with each subdomain. The best way to identify them is using our tool but to keep it fair, a few other popular tools are subjack and subdover.
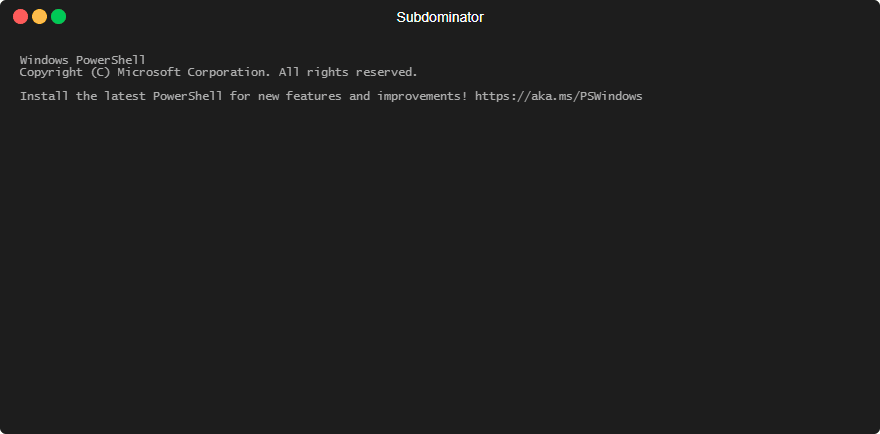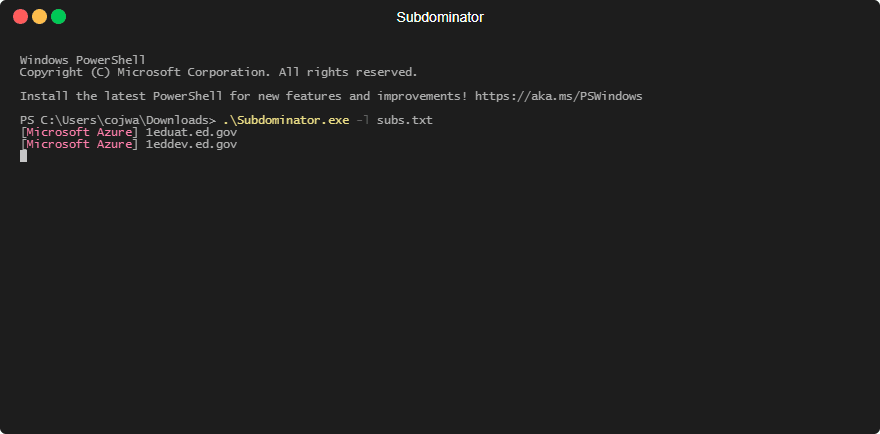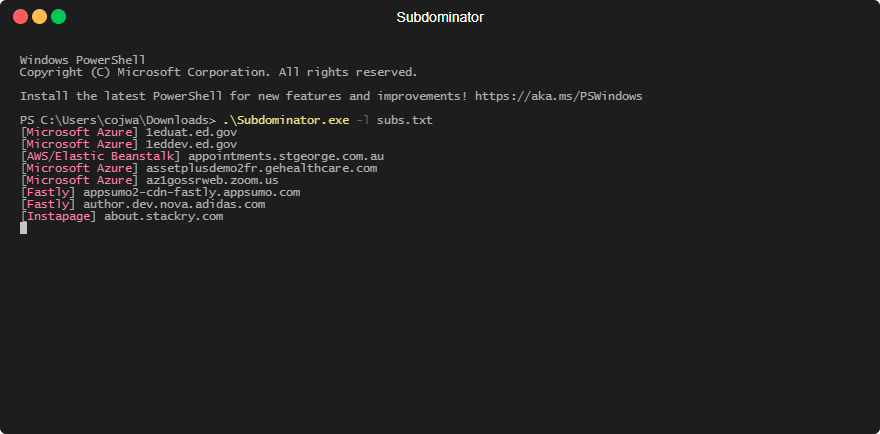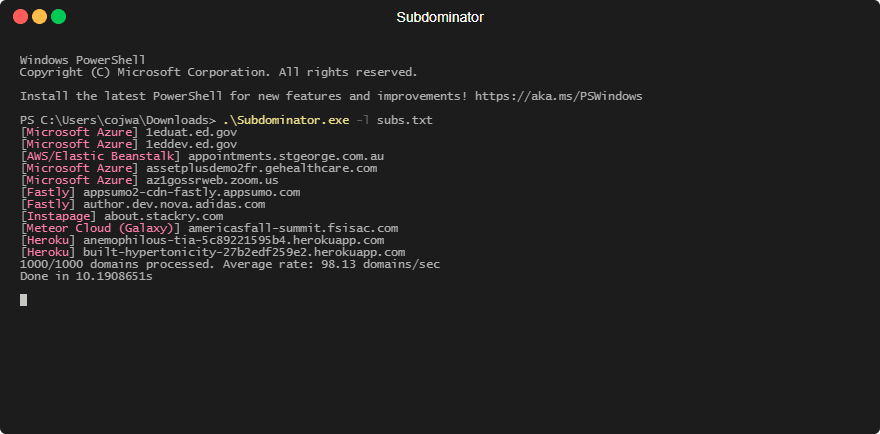
3. Validating/Taking over subdomains – Now that all the vulnerable domains have been identified, they can be taken over or validated. Note that it’s common to find false positives so manual validation is sometimes required. Each service has a different takeover/validation method but they are similar enough, to make it easy we have documented the process for Azure, AWS and others coming soon.
Exploitation of Subdomain Takeovers
Once a vulnerable subdomain has been identified, an attacker can exploit it in a few simple steps:
-
- Verify vulnerability – The first step is to verify that the subdomain is in fact vulnerable to takeover. False positives are common so manual validation steps should be performed depending on the service.
-
- Register subdomain – The next step is for the attacker to actually take the subdomain, once they know it is definitely exploitable they need to go to the applicable service and register the domain to their own account. The steps for this will vary depending on the service.
-
- Host content on attacker’s server – Now that the subdomain resolves to the attacker’s server, they can host any content they want under that subdomain. This often involves creating a basic web page announcing a subdomain takeover but could be any content.
-
- Draw traffic to compromised subdomain – To maximize impact, the attacker will look for ways to draw traffic to the compromised subdomain. This may include posting links on social media, registering the subdomain with search engines, or compromising linked domains.
-
- Capture traffic and launch further attacks – With access to the subdomain, the attacker can now capture any traffic and user data flowing through it. This foothold into the target domain can facilitate further exploitation through phishing, malware injection and more.
How to Fix a Subdomain Takeover
If you discover that a subdomain is vulnerable or has been taken over, there are a few steps you can take to remediate the issue:
-
- Delete the DNS record for the vulnerable subdomain. This will remove access for the attacker.
-
- If the vulnerable subdomain was intended to be used, create a new DNS record for it and point it at new infrastructure under your control. Make sure this infrastructure cannot be modified externally.
-
- Implement a process to continuously monitor your subdomains for unexpected DNS changes. There are services that can automate this process of subdomain monitoring and alerting.
-
- Check for any other potential impacts from the subdomain takeover, such as backlinks or other compromised assets. The attacker may have been able to leverage the takeover further than just the subdomain itself.
Additional Resources
Tools:
Related Posts: